How AI Could Fuel Demand for IT Security Software
As cybercriminals launch AI-powered attacks, IT security software becomes even more crucial.

Key Takeaways
Artificial intelligence (AI) is supercharging cyberattacks, increasing demand for security software.
Different kinds of software provide different degrees of protection, leading to a fragmented ecosystem of products.
Software firms can grow through mergers and acquisitions (M&A), as well as by introducing new services and features.
Your boss isn’t the only person excited about AI. Every hacker lurking on the dark web is, too.
Cybercriminals and nation states are starting to use AI to launch faster, more widespread attacks. For example, AI startup Anthropic recently disrupted a large-scale cyberattack whose perpetrators manipulated the company’s own Claude Code tool to facilitate the global cyberattack campaign.1
Incidents like these should spark even greater demand for IT security software to help thwart such intrusions.
Market intelligence firm IDC forecasts that spending on security software will rise by 14.4% year over year in 2025.2 Overall security spending, which includes services and hardware, is expected to keep expanding through 2028.
Some software companies worry that AI might directly compete with their products.
OpenAI recently announced the development of its own software for tasks like reviewing documents and managing sales leads.3 Following this announcement, the share prices of DocuSign and HubSpot — companies whose tools specialize in that kind of work — dropped.4
Nevertheless, the increased use of AI could potentially drive higher demand for IT security software.
Why Is the Demand for IT Security Software Rising?
If you follow the news, you know how frequent and costly cybersecurity incidents have become. It’s no wonder that spending on security software is on the rise.
In the U.S. alone, the FBI’s Internet Crime Complaint Center logged nearly 860,000 complaints in 2024.5 Figure 1 illustrates the recent rise in these incidents.
Figure 1 | U.S. Cybercrime Has Ticked Upward Over the Last Decade
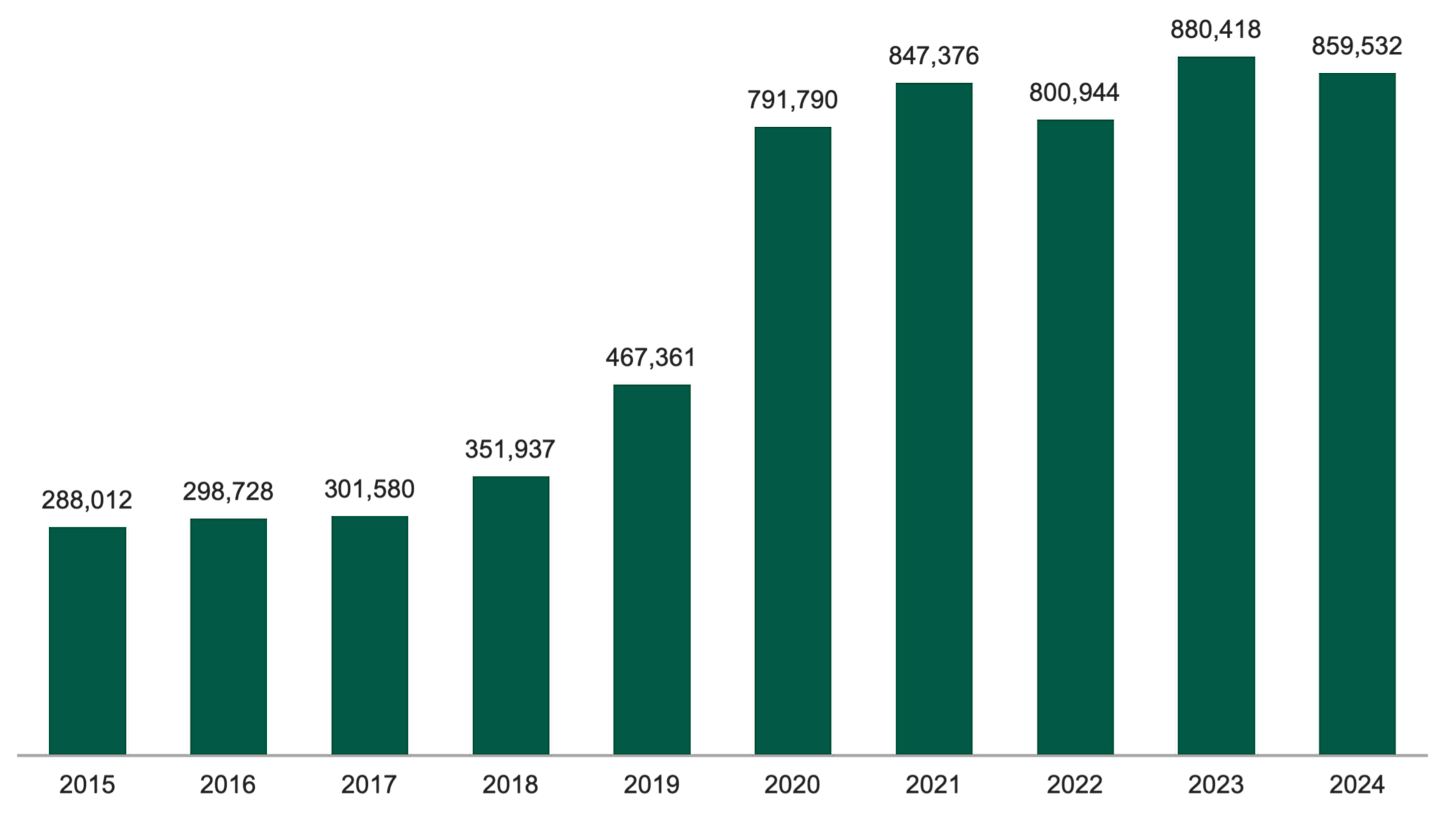
Data from 1/1/2015 – 12/31/2024. Source: FBI Internet Crime Complaint Center.
U.S. losses totaled $16.6 billion in 2024, marking a 33% increase from 2023.
It’s not just a U.S.-only problem: The Asia-Pacific region led the world last year with 34% of all incidents, a 13% jump from 2023.6
Meanwhile, more cybercriminals are adding AI to their toolkits. According to Microsoft, AI-powered phishing attacks trick their victims into clicking a fraudulent link 54% of the time, versus 12% for those who don’t use AI.7
The technology could be used to:
Develop harder-to-detect malware more quickly.
Automate phishing campaigns on a large scale.
Create deep-fake videos and audio to deceive victims.
Generate fraudulent emails and websites.
Identifying Opportunities in IT Security Software
Cybersecurity encompasses a wide range of software tools, largely because malicious actors have numerous ways to infiltrate and attack computer systems. New and evolving software, increasingly powered by AI, can help organizations push back against these challenges.
Most of these tools fall into at least one of the following categories:
Cloud Security: Protecting Data in the Cloud
More organizations now rely on cloud-based applications, so their data increasingly resides in the cloud. While the cloud offers significant advantages, safeguarding these assets can strain IT teams, who must manage multiple services and tools.
Cloud security software reduces the risk by monitoring a company’s cloud resources and alerting the organization’s IT professionals to problems.
As a sign of this field’s significance, Google has announced plans to buy Wiz, a cloud security platform, for $32 billion.8 It would be Google’s largest acquisition to date.
Identity and Access Management: Securing Networks
Identity security ensures that users and devices have the necessary permissions to access a company’s network and resources.
A few specialties have emerged in this area:
Identity governance and automation (IGA) software automates the creation and management of accounts and access. IGA also facilitates easier auditing and reporting on IT security.
Privileged access management (PAM) tools provide a higher level of security for an organization’s most sensitive systems and data.
Customer identity and access management (CIAM) software works with users outside the company, such as customers and vendors. Those users may need limited access for placing orders or submitting invoices.
Endpoint Security: Safeguarding Devices
Endpoints are the physical devices that connect to a company’s networks. This includes laptops, smartphones, servers, printers, cameras, and internet of things devices, such as smart thermostats and wearable fitness trackers.
Endpoint detection and response (EDR) software monitors devices and works to neutralize threats using antivirus or malware tools.
A related type of solution, extended detection and response (XDR), uses data from multiple parts of a company’s cybersecurity defenses to identify and address threats.
Network Security Software: Defending IT Systems
A company’s network connects all its information technology components — applications, data, and endpoint devices — so they can communicate securely and reliably.
In the past, network security typically employed a “moat and castle” strategy.
Firewalls and other security software acted as the moat, keeping intruders from gaining access to the network. But if you were “inside the castle,” you were trusted and could access most, if not all, resources.
Unfortunately, this approach is no longer as effective today. The modern workforce utilizes multiple services and apps, and these employees have also become geographically dispersed. This makes it harder to play defense.
In response, network security is shifting toward approaches such as secure access service edge (SASE) and zero-trust architecture (ZTA). Software solutions using SASE and ZTA constantly inspect and authenticate users and their requests for access.
For instance, Cloudflare has introduced a new security suite designed for AI-powered tools.
How M&A Is Shaping Security Software Growth
More security software companies are attempting to expand their reach by either increasing their service offerings or acquiring other businesses.
For example, Palo Alto Networks is bundling several services into a single solution. To do this, it’s acquiring CyberArk, a firm known for its identity security tools.9
In a fragmented field like security software, these deals represent a shift in how the industry operates.
According to a popular theory, no single company has dominated IT security because if one grew too large, it would become an irresistible target for hackers. The resulting increase in attacks would ultimately undermine that company.
AI has the potential to change this dynamic. An increasing number of companies are integrating AI into their security software, and AI models generally enhance their performance with more training data.
In this scenario, becoming a top player would turn into an advantage because your company would have access to more data. As the quality of the company’s software improved, it could then win even more market share.
However, consolidation could also act as a headwind if competition intensifies, forcing companies to lower their prices.
Navigating Opportunities in Risk-Driven Cybersecurity
Cybersecurity threats plagued businesses and other organizations even before the widespread adoption of artificial intelligence. If AI amplifies this risk, however, demand for IT security software could also intensify, thereby fueling business growth.
This corner of the software industry may also benefit as companies buy other firms or broaden their offerings.
That’s why we believe investors may still find solid opportunities in security software despite the potential challenges posed by AI within the wider software industry.
Authors
Senior Client Portfolio Manager
Explore More AI Insights
Read our latest articles about artificial intelligence.
Anthropic, “Disrupting the First Reported AI-Orchestrated Cyber Espionage Campaign,” November 13, 2025.
IDC, “Worldwide Security Spending to Increase by 12.2% in 2025 as Global Cyberthreats Rise, Says IDC,” Media Release, March 21, 2025.
OpenAI, “Building OpenAI with OpenAI,” September 29, 2025.
Investing.com, “HubSpot Stock Falls as OpenAI’s Internal Tools Spark Concerns for SaaS sector,” October 1, 2025.
FBI Internet Crime Complaint Center, “Internet Crime Report 2024,” April 23, 2025.
IBM and Red Hat, “IBM X-Force 2025 Threat Intelligence Index,” April 16, 2025.
Microsoft, “Microsoft Digital Defense Report 2025,” October 20, 2025.
Google, “Google Announces Agreement to Acquire Wiz,” March 18, 2025.
Palo Alto Networks, “Palo Alto Networks Announces Agreement to Acquire CyberArk, the Identity Security Leader,” July 30, 2025.
References to specific securities are for illustrative purposes only and are not intended as recommendations to purchase or sell securities. Opinions and estimates offered constitute our judgment and, along with other portfolio data, are subject to change without notice.
The opinions expressed are those of American Century Investments (or the portfolio manager) and are no guarantee of the future performance of any American Century Investments portfolio. This material has been prepared for educational purposes only. It is not intended to provide, and should not be relied upon for, investment, accounting, legal or tax advice.
Investment return and principal value of security investments will fluctuate. The value at the time of redemption may be more or less than the original cost. Past performance is no guarantee of future results.